OpenSSL PKCS#11 Engine
Engine_pkcs11 is an implementation of an engine for OpenSSL. It can beloaded using code, a configuration file, or the command line and passesany function call by openssl to a PKCS#11 module. Engine_pkcs11 ismeant to be used with smart cards and software for using smart cards inPKCS#11 format, such as OpenSC. Originally, this engine was part ofOpenSC until OpenSC was split into several small projects to improveflexibility.
 There is no official package available for openSUSE Leap 15.2
There is no official package available for openSUSE Leap 15.2 COMPATIBILITY - The pkcs11-helper library is available in POSIX and WIN32 compliant systems. 07 Open source library that will simplify interaction with PKCS#11 providerPKCS11-Helper is a library that simplifies the interaction with PKCS#11 providers for end-user applications using a simple API and optional OpenSSL engine. The Cryptographic Token Interface Standard, PKCS#11, is produced by RSA Security and defines native programming interfaces to cryptographic tokens, such as hardware cryptographic accelerators and smartcards. Existing applications that use the JCA and JCE APIs can access native PKCS#11 tokens with the PKCS#11 provider. You could also use pkcs11-spy to see what is happening at the interface between engine-pkcs11.so and opensc-pkcs11.so Andreas On 05:06 PM, Adam Zimmerman wrote: Hi Andreasopenssl does work directly, after I make the change you mentioned in your other email (putting the slot number in), as well as setting up a template in my openssl.conf file.
Distributions
openSUSE Tumbleweed
SUSE SLE-11 SP 4
Unsupported distributions
openSUSE:11.4
openSUSE:12.1
openSUSE:12.2
Openssl Pkcs11

openSUSE:12.3
openSUSE:13.1
openSUSE:13.2
openSUSE:Leap:42.1
openSUSE:Leap:42.2
openSUSE:Leap:42.3
openSUSE:11.1
SUSE:SLE-12:SLE-Module-Toolchain
SUSE:SLE-11:SP3
DISCONTINUED:openSUSE:11.1
This article describes how to set up a Smart Card/HSM backed OpenSSL CA using a Smart Card HSM or any PKCS11 enabled device.
Background
Since some years back I use WPA2 Enterprise with EAP-TLS (Certificate authentication) for my wifi at home. Historically I have used certificates from a public CA for this purpose. This is not best practice since you don’t have control over the certificates that are issued.
Also, I recently bought a new switch capable of 802.1X authentication on all ports. For this purpose I want all my machines (even those without wifi) to have certificates. So I decided to go through the hassle of setting up my own private CA.
Setting up CA
For the basic setup of the CA I followed Jamies excellent guide on setting up a CA. So in this post you can assume that all the basic stuff like folders structure and basic commands are the same. I will only show you the differences needed to have the Root CA key stored on a PKCS11 device like a HSM, Smart Card HSM or a Yubikey. I will even try to follow his topic names so you can follow along.
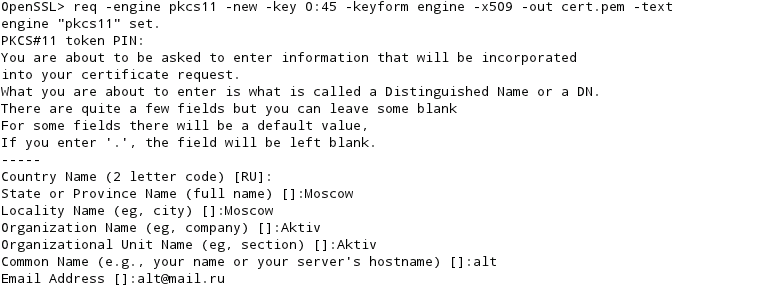
Configure PKCS11 Engine
I will not discuss the operating system part of getting PKCS11 devices to work in this article. But basically you just need to install some packages, you can read about it here.
First of all we need to configure OpenSSL to talk to your PKCS11 device. This can be done from configuration or interactively on the command line.
From conf:
From cli:
Create the root pair
First of all we need to have a RSA key pair on the PKCS11 device:
Create the root certificate
I will assume that you have configured pkcs11 in openssl.cnf (otherwise you will have to first run the engine command in openssl interactively before any other command).
Create the intermediate pair
For the intermediate key pair I followed jamies guide. I need frequent access to this CA so I have decided to have the intermediate pair on file instead of HSM.
Openssl Pkcs11 Engine Slots
Create the intermediate certificate
I changed one thing in jamies intermediate/openssl.cnf because I dont see the point of having province set in the CAs
To use the Root key stored on pkcs11 to sign the intermediate certificate use this command:
We now have all we need to sign certificates. Just follow Jamies guide Sign server and client certificates
References
Openssl Pkcs11 Engine Slot Kit
It took me a few hours to get this going because of sort of a lack of documentation on how to use OpenSSL and PKCS11 together, during my efforts I found these resources helpful